When you think about security in the cloud, always consider the multi-layer approach. It defines the multiple layers of security controls in the cloud to ensure that if a security attack is not caught in one layer, it will most likely be caught in the next. The multiple layers increase the overall security score of the environment and reduce the probability of a security breach by a huge margin.
Different security layers in a cloud environment as follows:
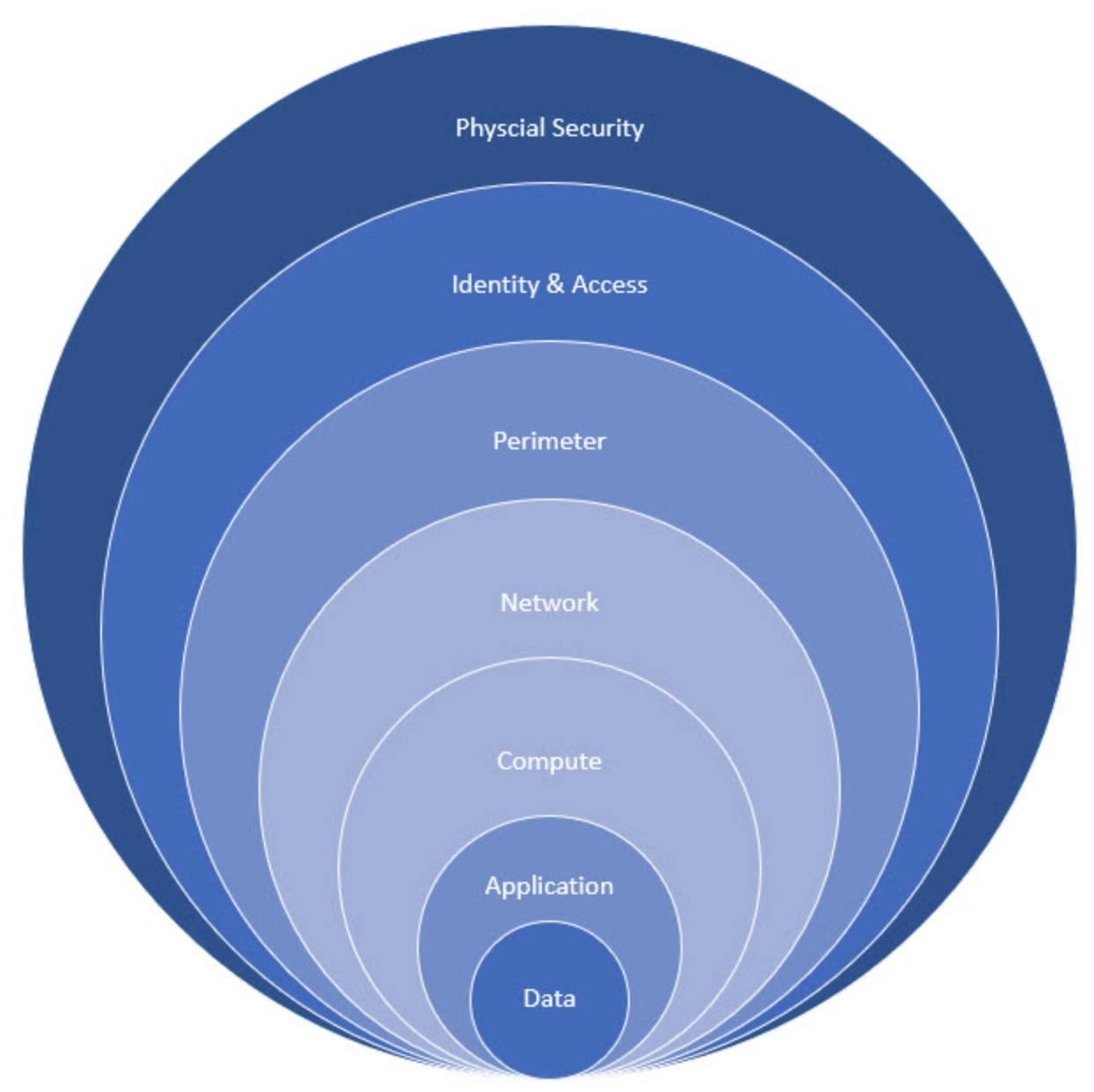
Cloud security is a shared responsibility. Each layer of security is responsible for the cloud provider or the customer. Today I am going to give an overview of cloud security in Azure with consideration of multilayer approach.
- Physical Security: Microsoft owns the Azure data centers and manages physical security at all of the locations. Only authorized personnel have access to different areas of the data centers.

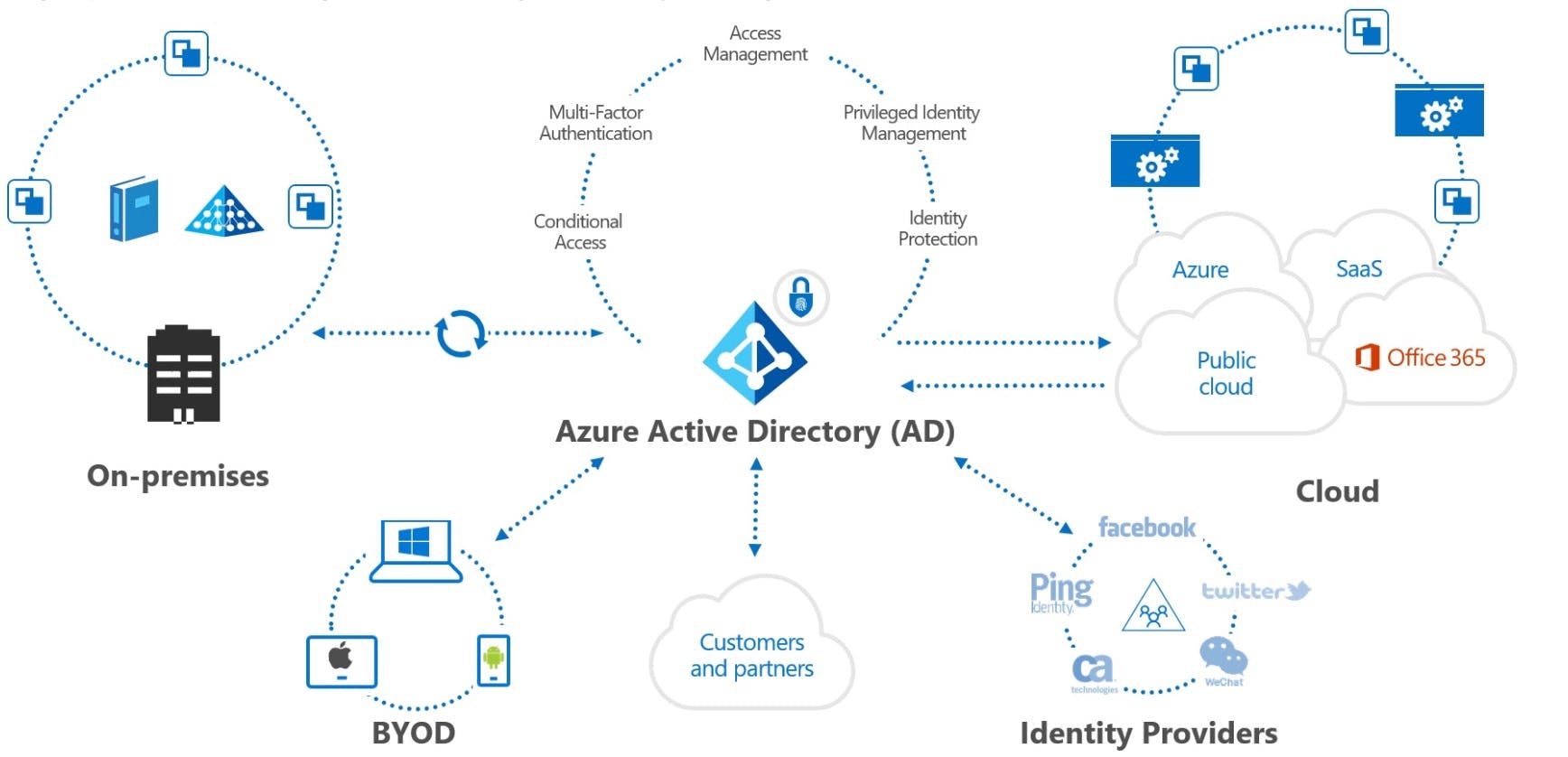
- Identity & Access Management: All Azure resources are governed and controlled through Azure Active Directory, which is also known as the central identity plane. Azure Active Directory (AD) is Microsoft's cloud-based identity and access management (IAM) service; it can be used to manage secure user sign-in to thousands of external services, such as Microsoft Office 365, the Azure portal, and other SaaS applications. Furthermore, you can control access to your Azure resources using Role-based access control (RBAC). Users can be granted higher privileges just-in-time using Azure Privileged Identity Management.
- Perimeter: By default, Azure enables basic Distributed denial of service (DDoS) protection which comes with always-on traffic monitoring, and real-time mitigation of common network-level attacks. The standard tier of DDoS protection provides additional capabilities to protect against volumetric attacks, protocol attacks, and application attacks.

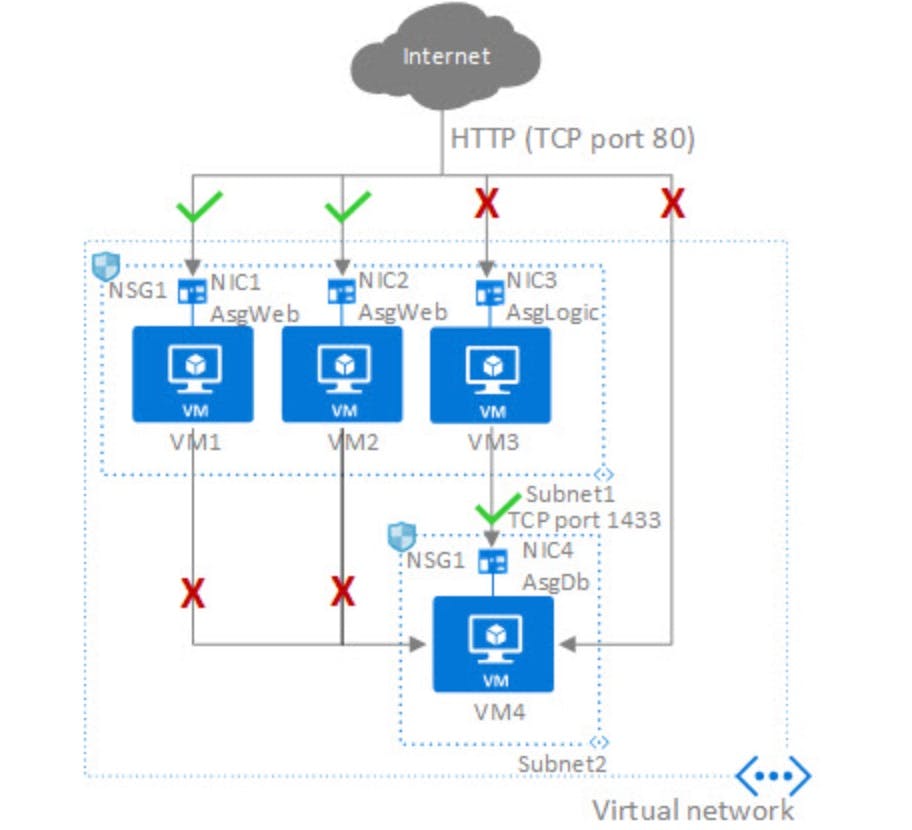
- Network: A network security group (NSG) in Azure is the way to activate a rule or access control list (ACL), which will allow or deny network traffic to your virtual machine instances in a virtual network. NSGs can be associated with subnets or individual virtual machine instances within that subnet. When an NSG is associated with a subnet, the ACL rules apply to all Virtual Machine instances of that subnet. In addition, you can further restrict traffic to an individual virtual machine by associating an NSG directly to that virtual machine.You can filter network traffic to and from Azure resources in a virtual network through Network Security Groups which contains security rules allowing or denying traffic. Under Azure Security Center’s standard pricing tier, you can lock down inbound traffic to your Azure VMs with Just In time VM access (eg – RDP, SSH).
- Compute: Azure Security center provides protection against threats by its ability to process signals and detect security threats like RDP brute-force attacks and SQL injections. The security center also gives a Secure score based on the assessment of the security posture of your environment.
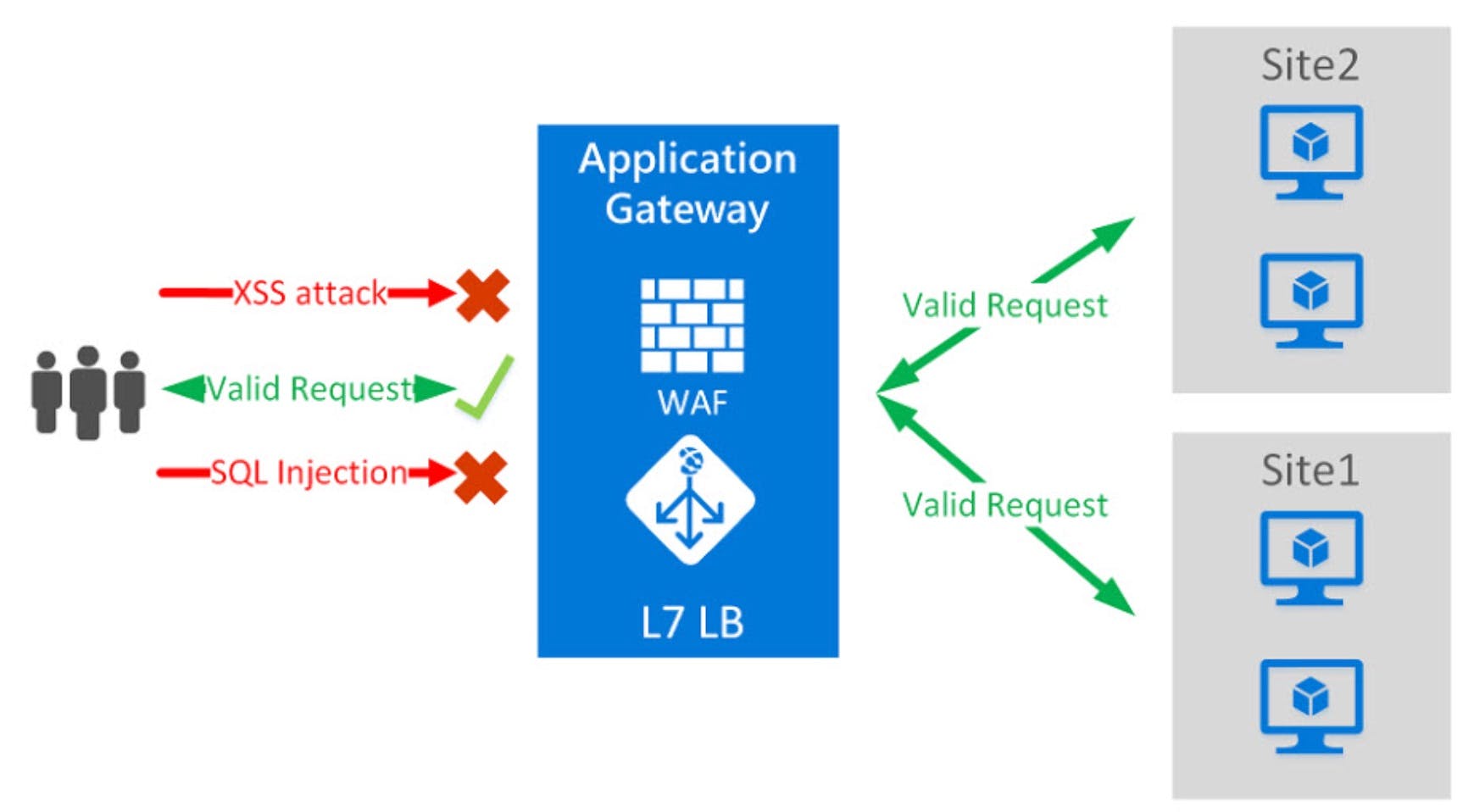
- Application: Application Gateways and Web Application Firewall provides centralized protection of your web applications from common exploits and vulnerabilities. Azure Front door is another service that allows you to author custom Web Application Firewall (WAF) rules for access control to protect your HTTP/HTTPS workload from exploitation based on client IP addresses, country code, and Http parameters. A managed identity from Azure Active Directory (AAD) allows your app to easily access other Azure Active Directory-protected resources such as Azure Key Vault. The identity is managed by the Azure platform and does not require you to provision or rotate any secrets. Also, you can enable SSL on your app services.
- Data: We need make sure to encrypt the Data-at-rest for both structured and unstructured data. You can further control the access to the data using authentication mechanisms.
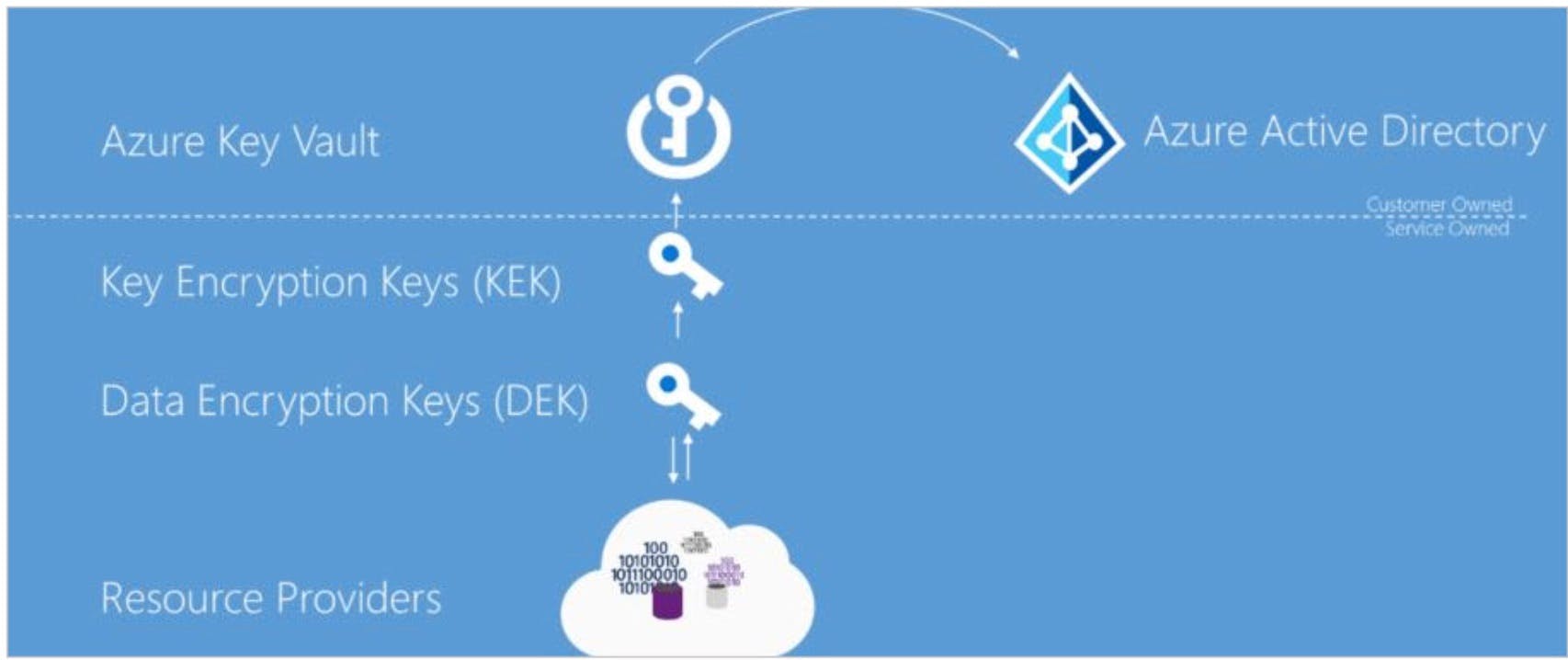
Azure offer Cloud based KMS aka Azure Key Vault A managed service with a pay-as-you-go model which means that the customer doesn’t have to manage the underlying software/hardware. Also, other services within the Azure environment are seamlessly integrated with Azure Key Vault. Secure key management is essential to protect data in the cloud. Use Azure Key Vault to encrypt keys and small secrets like passwords that use keys stored in hardware security modules (HSMs). For more assurance, import or generate keys in HSMs, and Microsoft processes your keys in FIPS 140-2 Level 2 validated HSMs (hardware and firmware). With Key Vault, Microsoft doesn’t see or extract your keys. Monitor and audit your key use with Azure logging—pipe logs into Azure HDInsight or your security information and event management (SIEM) solution for more analysis and threat detection.
Storage services in Azure such as Azure Blob Storage and Azure file Shares are using a service called Azure Storage Service Encryption (SSE) that uses AES-256 encryption. This feature is enabled by default for storage accounts and cannot be disabled and is transparent for users.
Now we need to encrypt the Data-in-transit. Azure offers many mechanisms for keeping data private as it moves from one location to another.
TLS encryption in Azure Microsoft gives customers the ability to use Transport Layer Security (TLS) protocol to protect data when it’s traveling between the cloud services and customers. Microsoft datacenters negotiate a TLS connection with client systems that connect to Azure services. TLS provides strong authentication, message privacy, and integrity (enabling detection of message tampering, interception, and forgery), interoperability, algorithm flexibility, and ease of deployment and use.
Other In transit encryptions
HTTPS for access over console or Rest API and Shared Access Signatures (SAS), which can be used to delegate access to Azure Storage objects, include an option to specify that only the HTTPS protocol can be used when you use Shared Access Signatures. This approach ensures that anybody who sends links with SAS tokens uses the proper protocol.
SMB encryption SMB encryption is turned on for a share or server, only SMB 3.0 clients are allowed to access the encrypted shares.
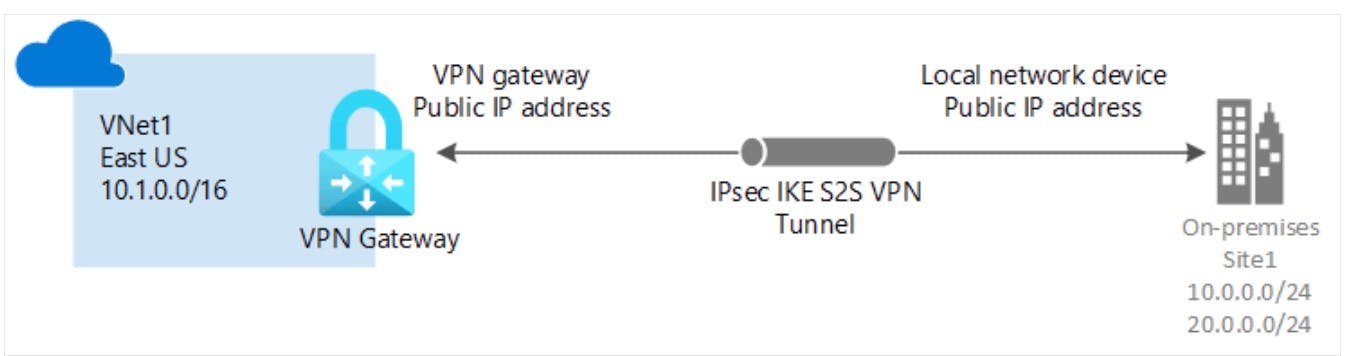
Azure VPN encryption You can connect to Azure through a virtual private network that creates a secure tunnel to protect the privacy of the data being sent across the network.
Azure VPN gateway Azure VPN options like Point-to-site VPNs and Site-to-site VPNs are using IPsec for secure tunneling
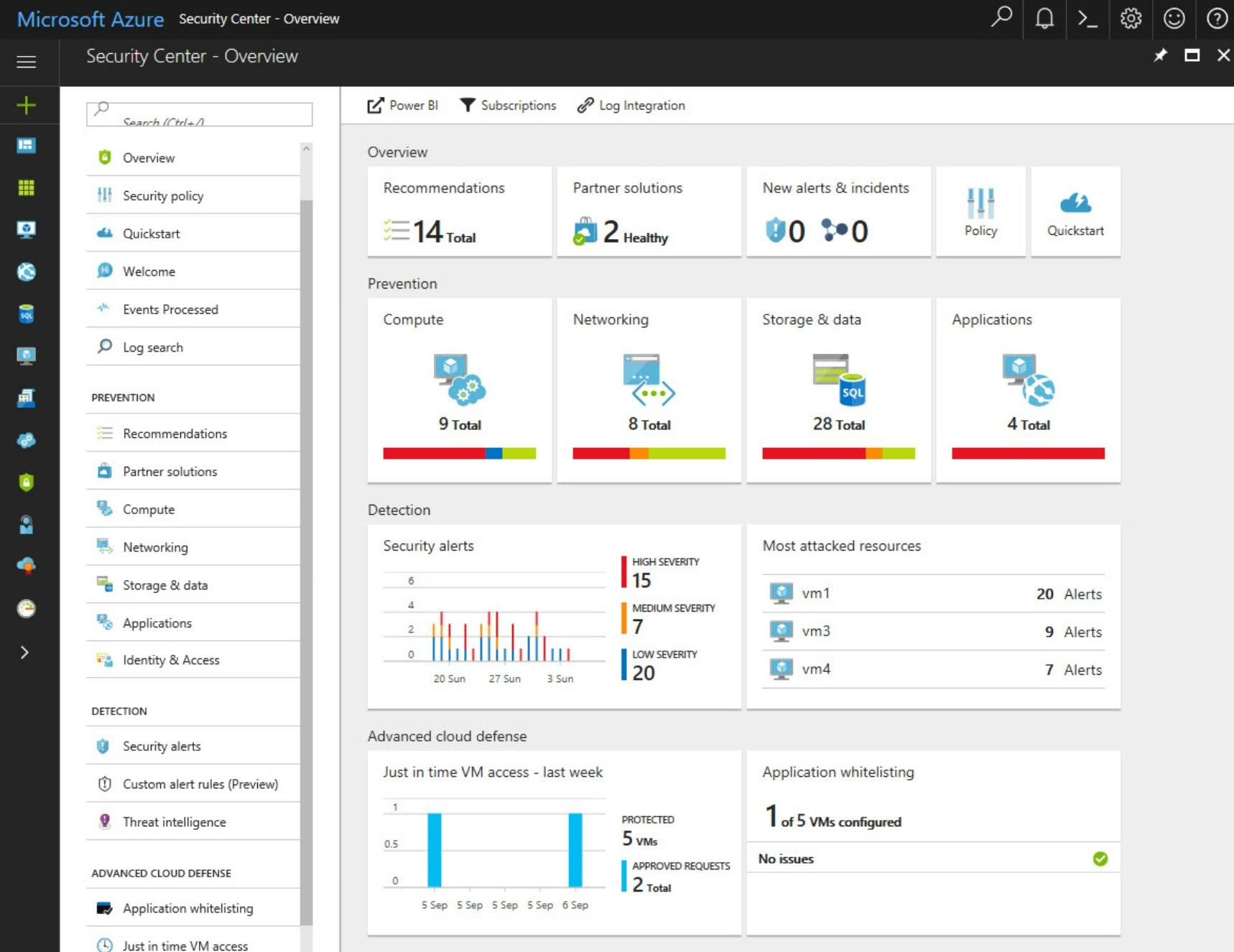
- Microsoft Defender for Cloud is a great tool that can help in strengthening your security posture in Azure. It provides advanced threat protection across hybrid workloads. It protect your multi-cloud and hybrid environments.
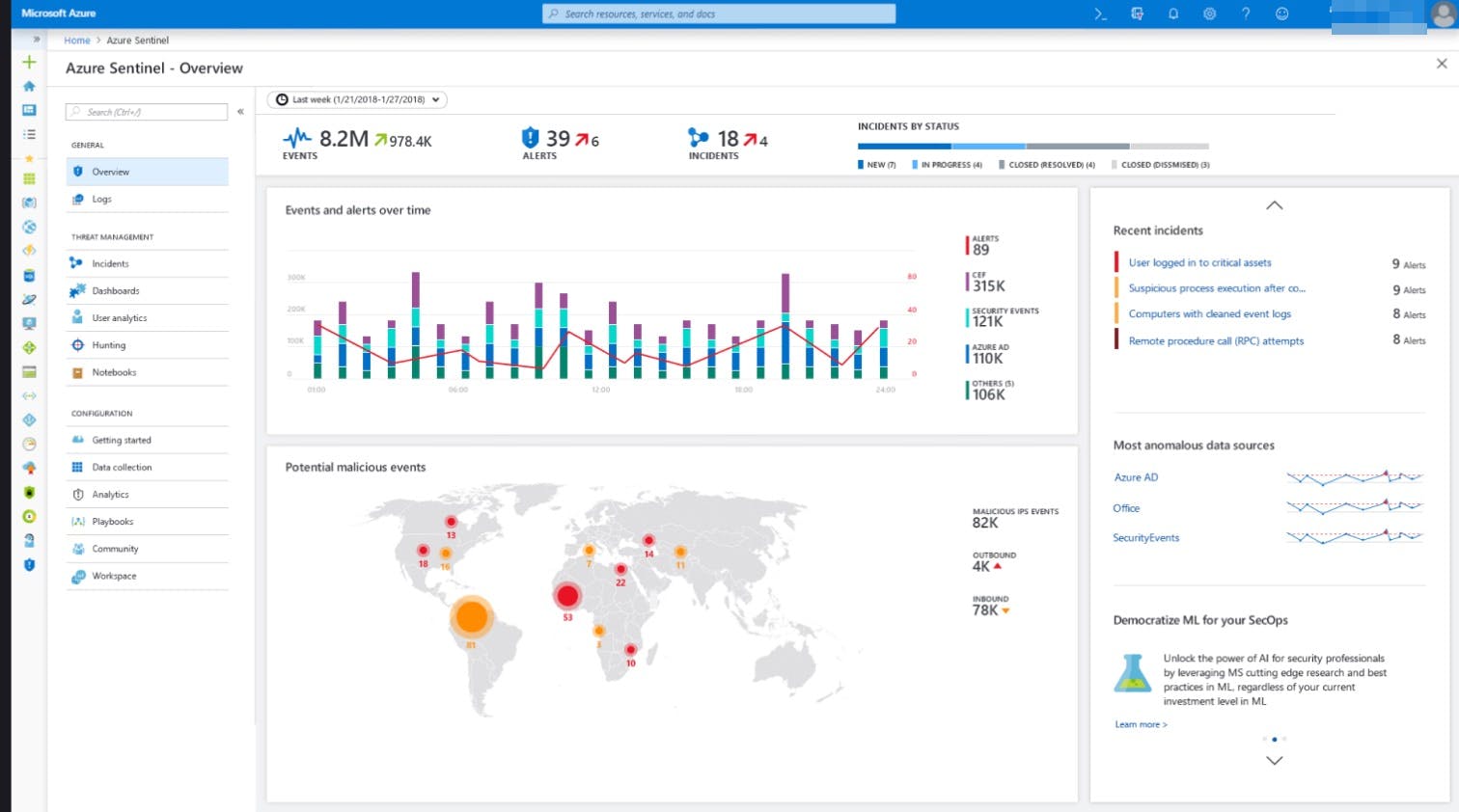
- Azure Sentinel is a cloud-native Security Information Event Management (SIEM) solution that delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting, and threat response. It supports Logic apps-based Security Runbooks which can run in response to an alert.
Conclusion: In this blog we learn how to secure the Azure cloud with multi-layer approach.Each layer works together to provide a cohesive security solution.
Reference documents
azure.microsoft.com/en-us/products